Code Project: CVE Hunter with Cursor AI
A Practical Side Project for Real-World Cyber Threat Intelligence
In the age of AI-assisted development, I challenged myself to build something that not only showcases technical skills but also solves a real problem I face everyday. That’s how CVE Hunter was born.
As a cybersecurity professional, I frequently look up CVEs (Common Vulnerabilities and Exposures). But here’s the issue: the information I need is fragmented across the internet. One website has CVSS scores but no exploit data, another has exploit references but lacks EPSS probabilities, and CVEDetails—once a go-to source—now hides most useful features behind a paywall. It was frustrating.
So I decided to build a unified CVE intelligence dashboard that aggregates all the relevant details I care about—faster, cleaner, and AI-powered.
Step 1: Setting Up the CVE Data Pipeline (NVD API)
I started with the National Vulnerability Database (NVD), which offers a public API for querying CVEs. To make queries faster and more flexible, I wrote a Python script that:
- Pulls CVE data via the NVD API
- Saves all CVEs in a local database (with full JSON blob for flexibility)
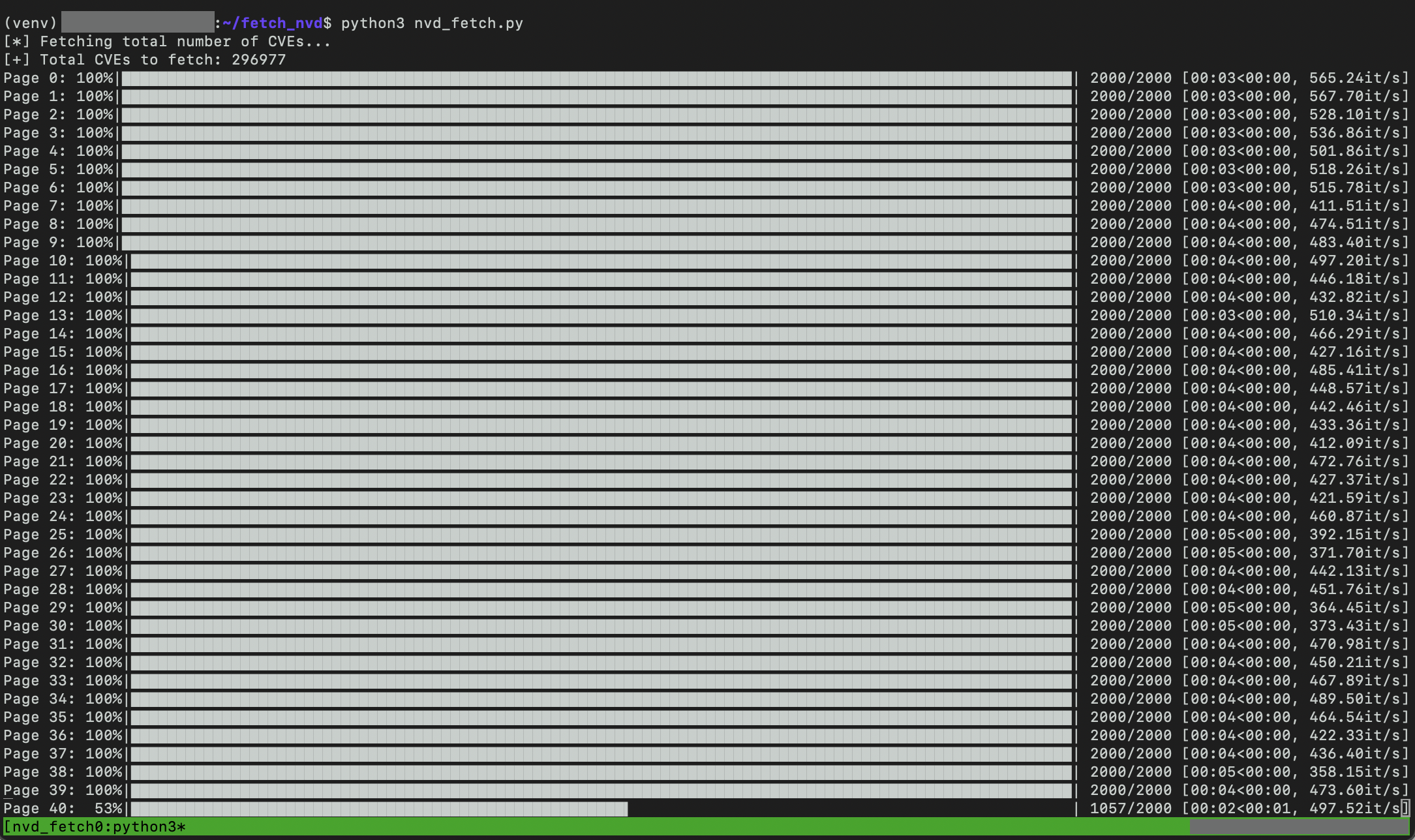
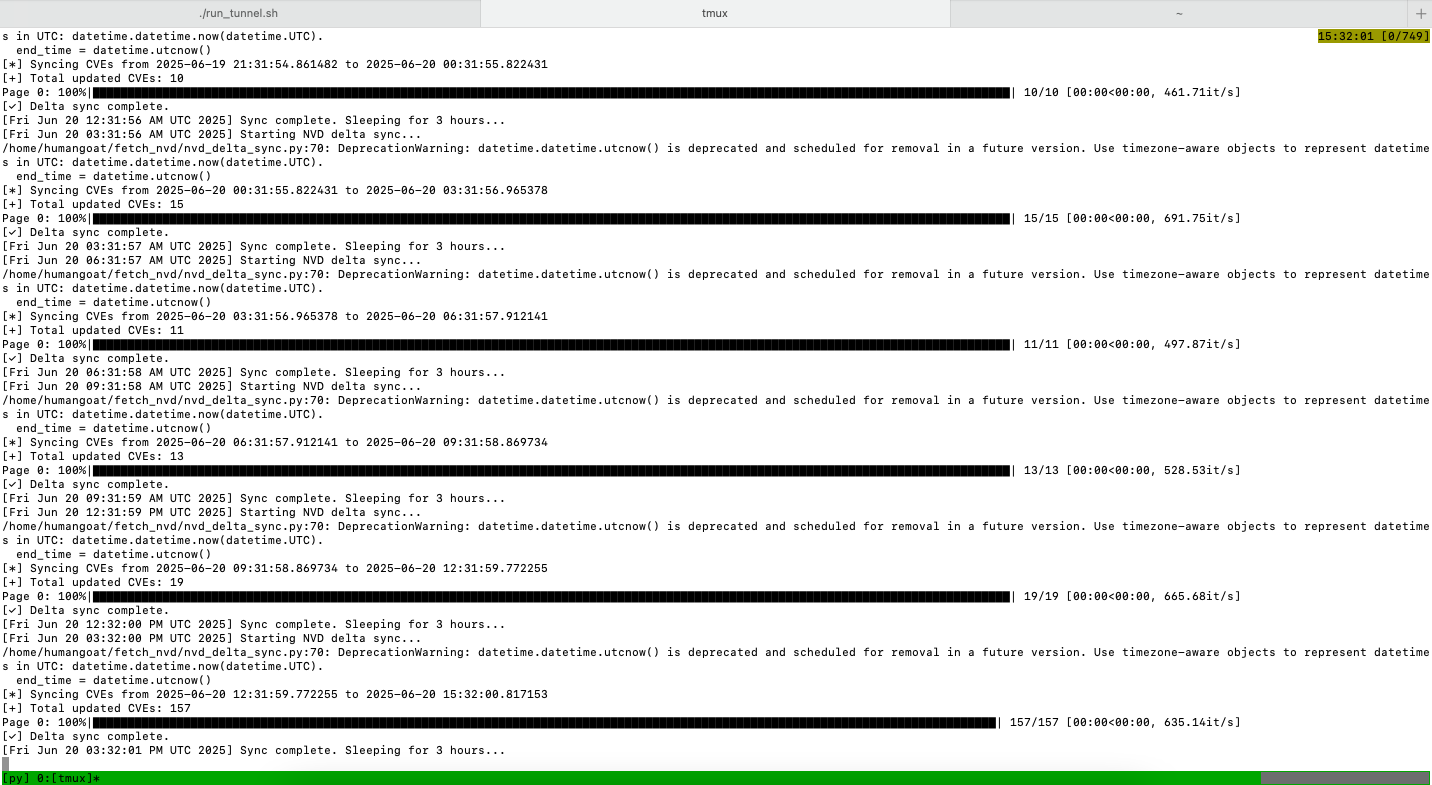
- Auto-syncs every 3 hours to fetch new or modified CVEs (NVD’s limit is 1 request every 2 hours)
Check out NVD API Best Practices for Developers
This created a robust and scalable backend to power the rest of the application.
Step 2: Building the CVE Hunter Interface
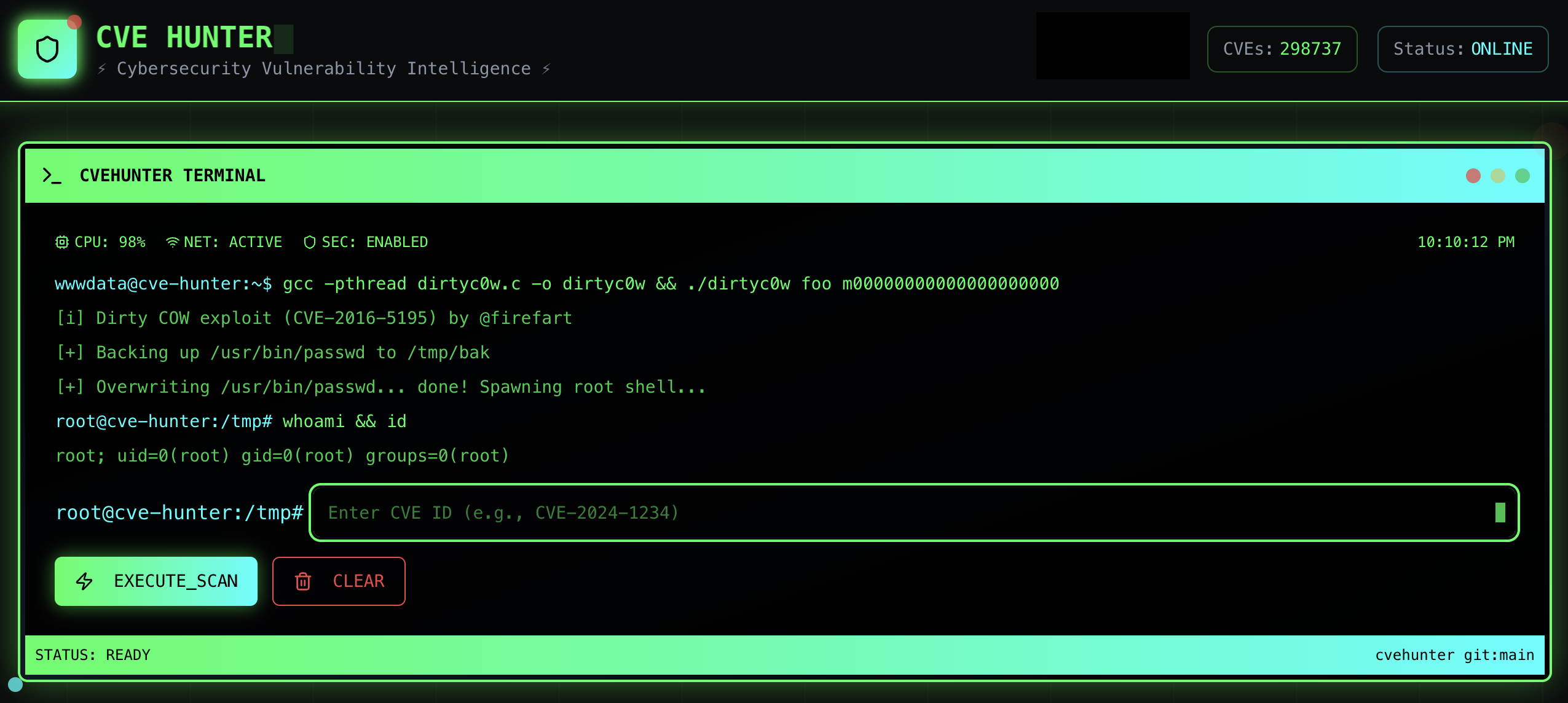
With the data foundation in place, I started designing the frontend with a clean, focused UI. The core interface includes:
- CVE Search Bar (by ID or keyword)
- CVE Details (summary, publish date, vendor info)
- Mitigation Tips (if available)
- EPSS Scores (for real-world exploit probability)
- CVSS Scores (base, temporal, and environmental)
- CWE Data (classification of the vulnerability)
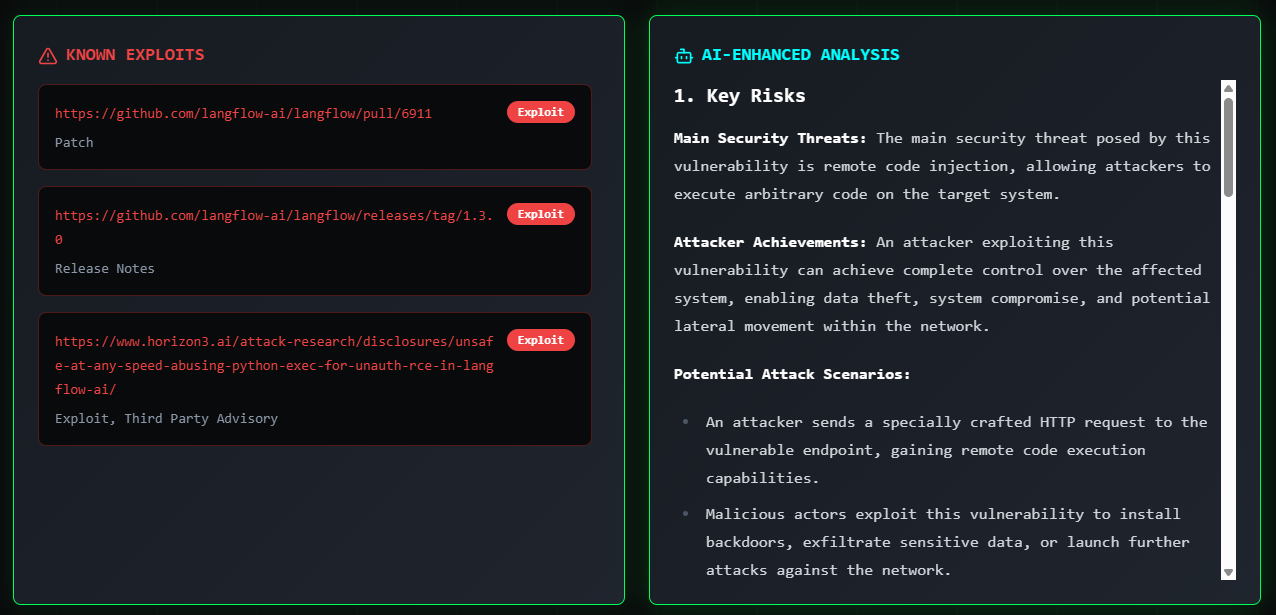
- Known Exploits (links to Proof of Concept code, malware usage, etc.)
- Risk Matrix (custom scoring based on impact and likelihood)
- References (blog posts, vendor advisories, security research)
- AI-Powered Analysis (using OpenAI API to summarize the threat, suggest mitigations, and even generate detection ideas)
The result? A single-pane-of-glass for CVE analysis.
Step 3: Design & Extras
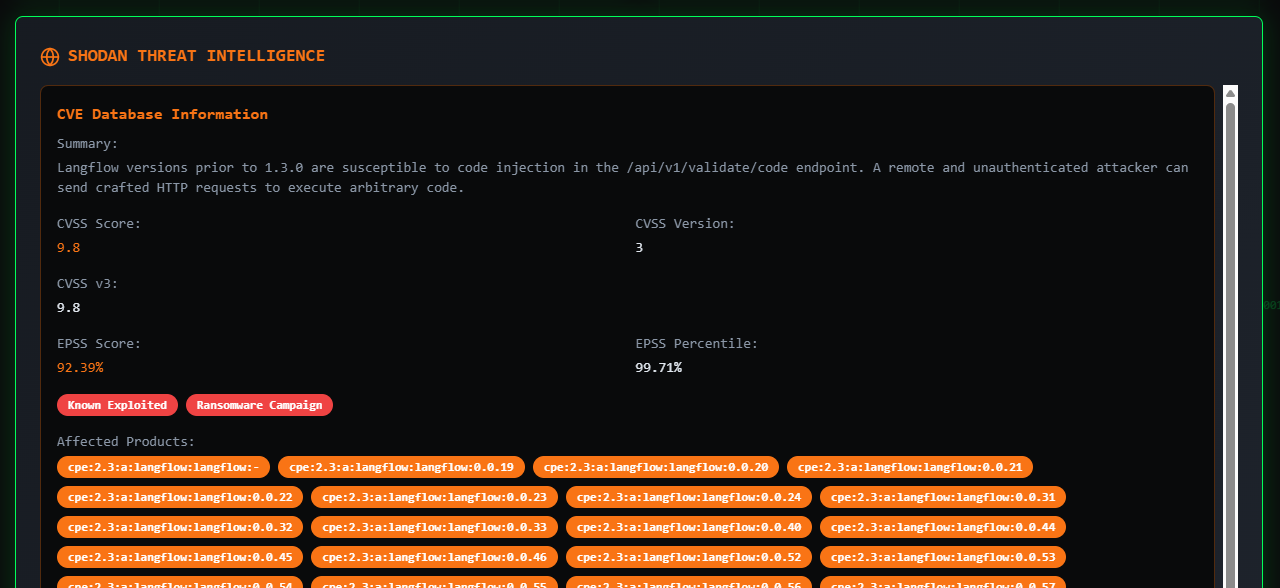
I themed the app with a Cyberpunk aesthetic, to keep the vibe fresh and developer-friendly. To make the platform more robust, I added Shodan CVE data, which brings in exploit context—whether the CVE is being actively exploited, associated with ransomware, or exposed in the wild.
What the Site Shows Today
- 🔢 Total CVEs Indexed and Beautiful Search Box Design
- 🔍 Detailed CVE View, CWE Classification, CVSS Scores, EPSS Scores
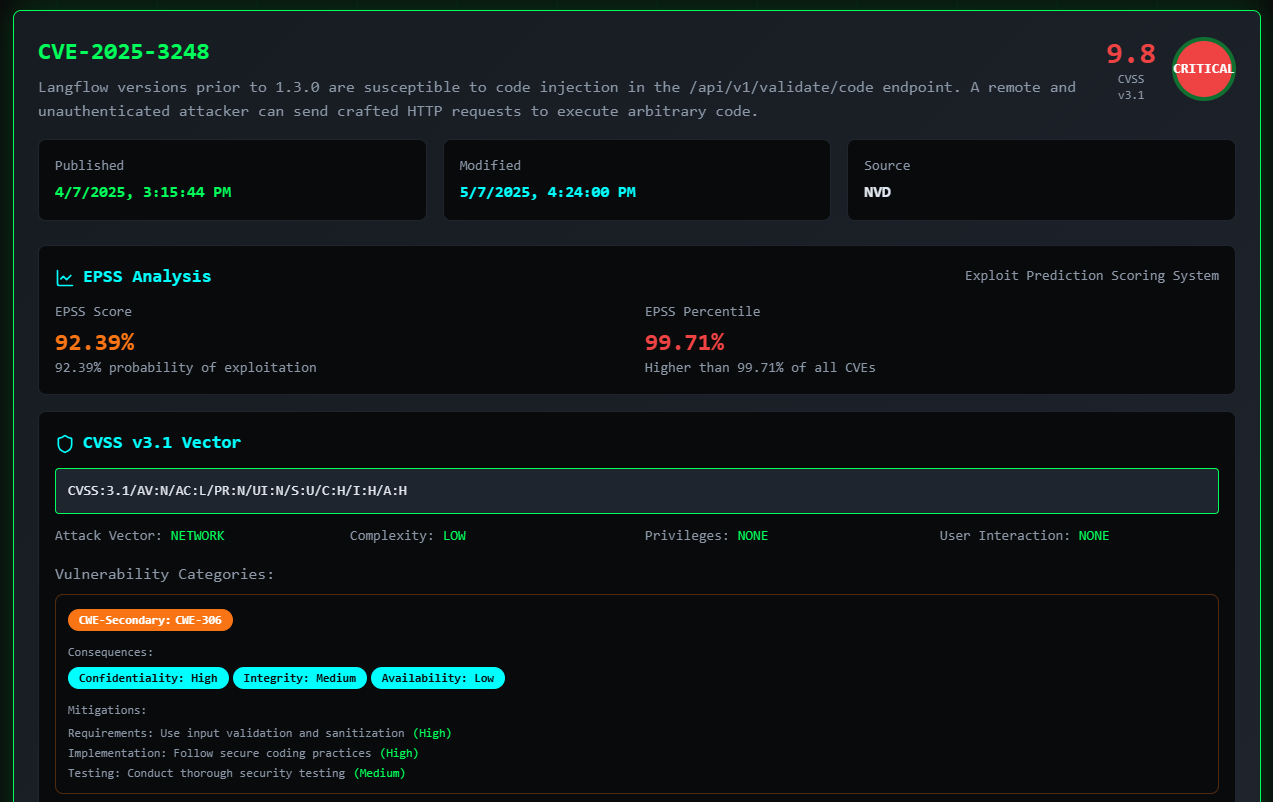
- ⏳ Beautiful Loading Screen
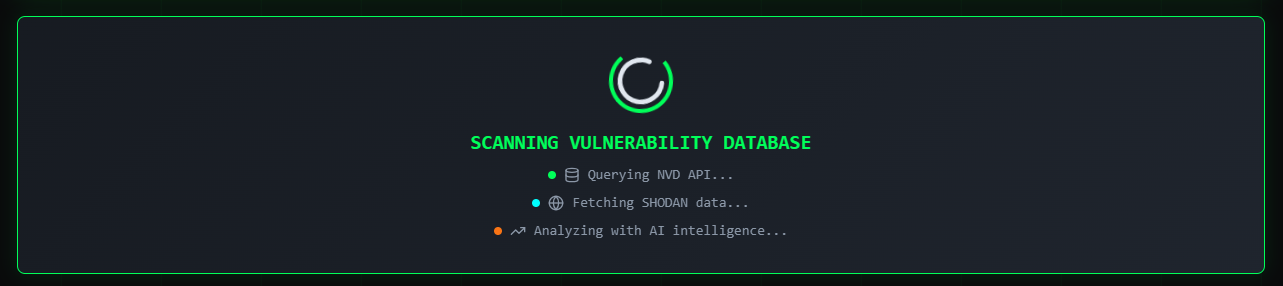
- 🧮 Custom Risk Matrix (Impact x Likelihood) and References
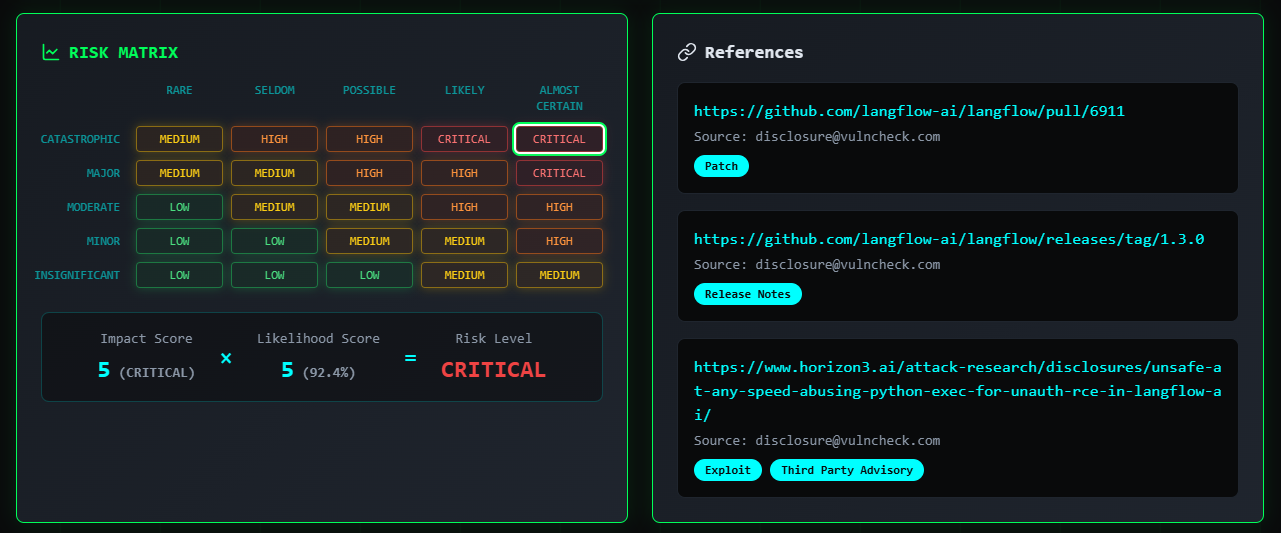
- ⚠️ Threat Intel and Threat Context
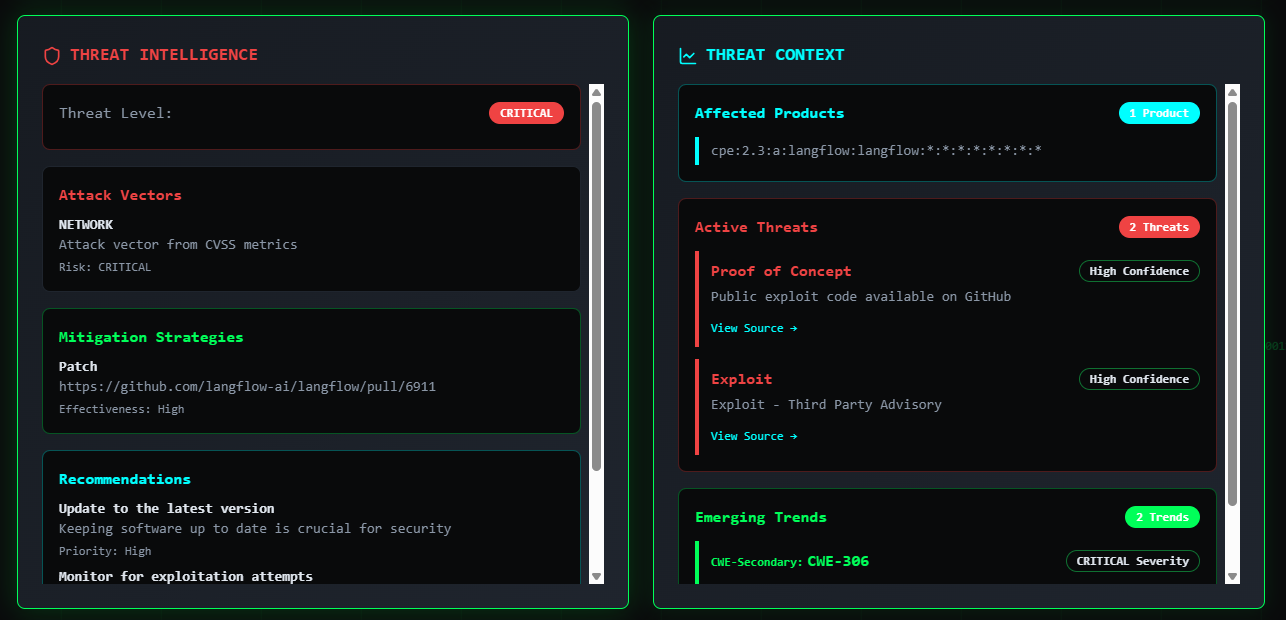
- 🔓 Known Exploits and AI Analysis
- 🌐 Shodan CVE Database and Intel
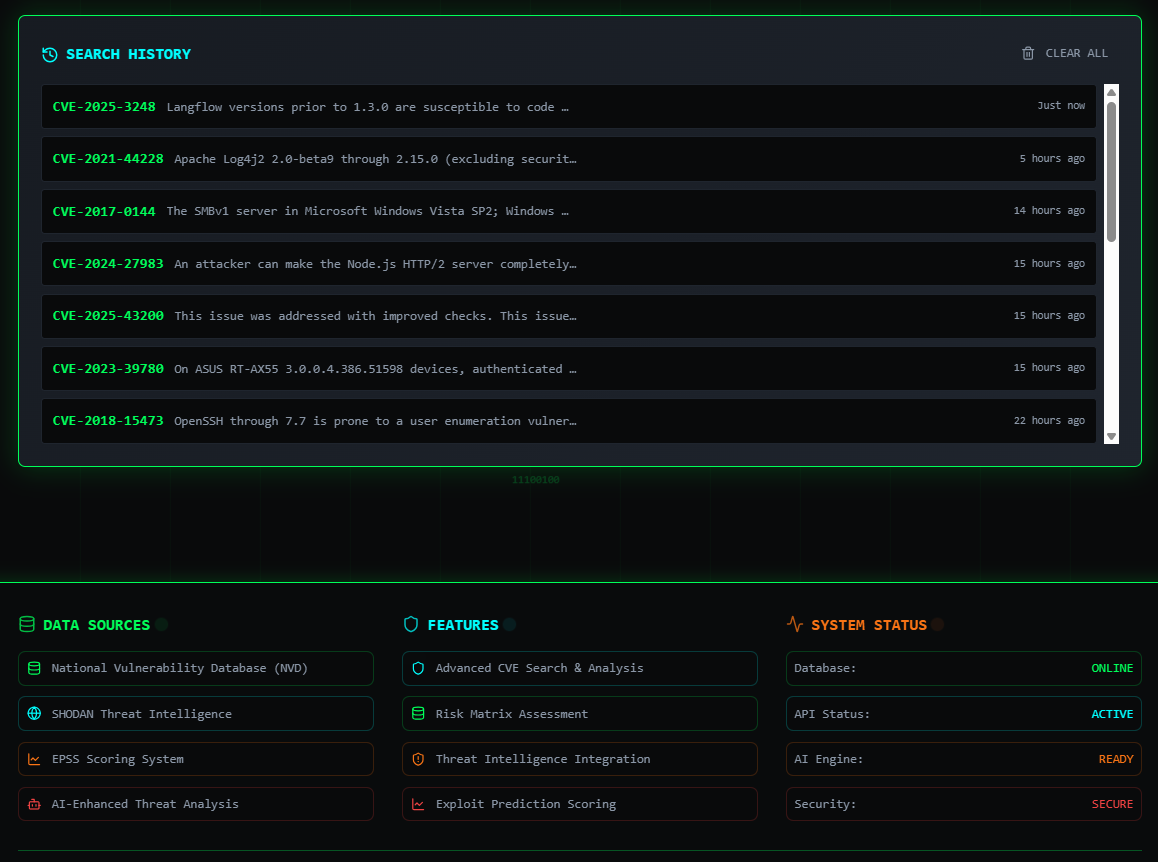
- 🕵️ Search History & Stylish Footer
Honestly? I’m pretty happy with how it turned out.
Roadmap: What’s Next
This is just the beginning. Here’s what I plan to add next:
-
🗺️ Shodan Search Integration with Interactive Map
Visualize IPs, locations, and open ports tied to CVEs in real time.
-
🔗 More Threat Intel Sources
Integrate APIs from vendors like GreyNoise, AlienVault OTX, and Recorded Future for richer context.
-
🔍 Full-text CVE Search & Filters
Severity, vendor, exploitability score, affected product—you name it.
-
🔐 Red Team/Blue Team Tabs
Different views for defensive mitigations vs. offensive testing strategies.
CVE Hunter started as a side project, but it quickly became something I now use everyday. It not only saves time, but it also improves the depth of my CVE analysis by combining structured data with AI insights.
It’s a reminder that even small personal projects—when built with intention—can have a big impact.
